Emerging Software Security Risks: How Are Tech Leaders Preparing for 2024?
Software security vulnerabilities can arise from a variety of sources — especially those related to emerging tech. Read on to find out which potential risks are most concerning to tech leaders.
One minute insights:
 Around half of leaders experienced software-related security issues during the past six months
Around half of leaders experienced software-related security issues during the past six months The most common sources of security issues were open source software, purchased software and legacy code
The most common sources of security issues were open source software, purchased software and legacy code Open source code is viewed by many as a potential risk source, and organizations use vulnerability assessments (VAs) to gauge their risk exposure
Open source code is viewed by many as a potential risk source, and organizations use vulnerability assessments (VAs) to gauge their risk exposure Many plan to increase the resources allocated to protecting against software security risks
Many plan to increase the resources allocated to protecting against software security risks Tech leaders feel informed about emerging risks and are confident they can protect against them
Tech leaders feel informed about emerging risks and are confident they can protect against them
Around half of leaders experienced software-related security issues recently, often due to open source code
During the past six months, did your organization experience a security issue(s) related to software?
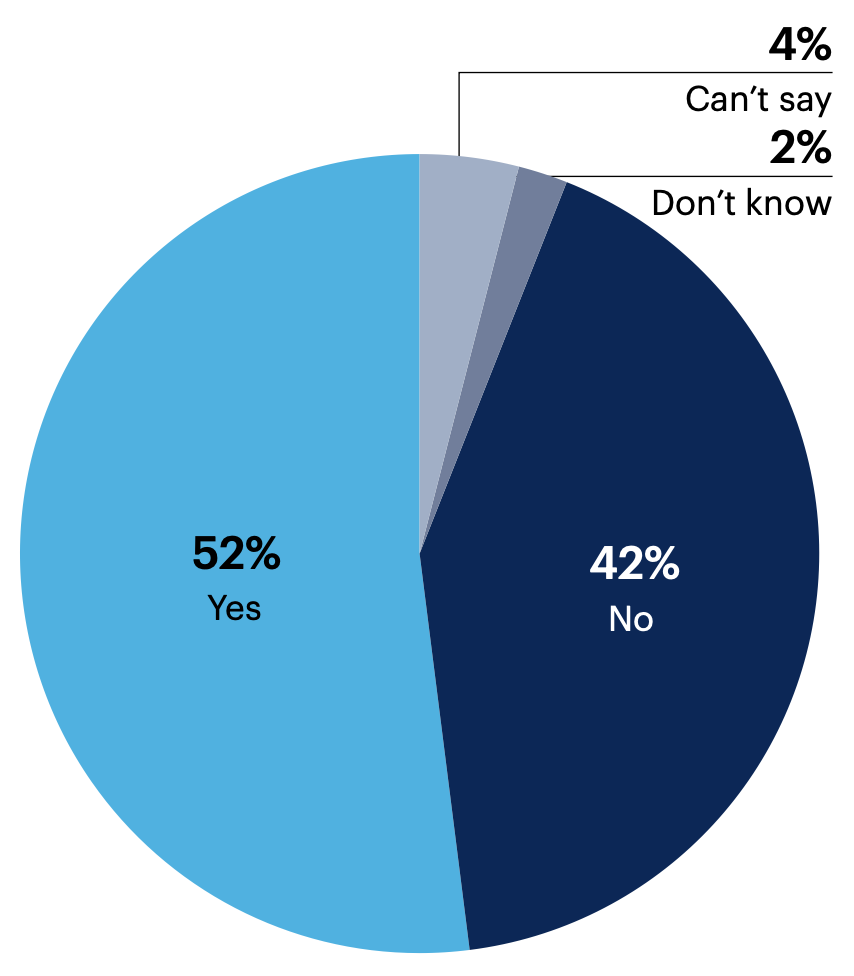
52% of all respondent organizations (n = 125) experienced a software-related security issue within the past six months.
n = 125
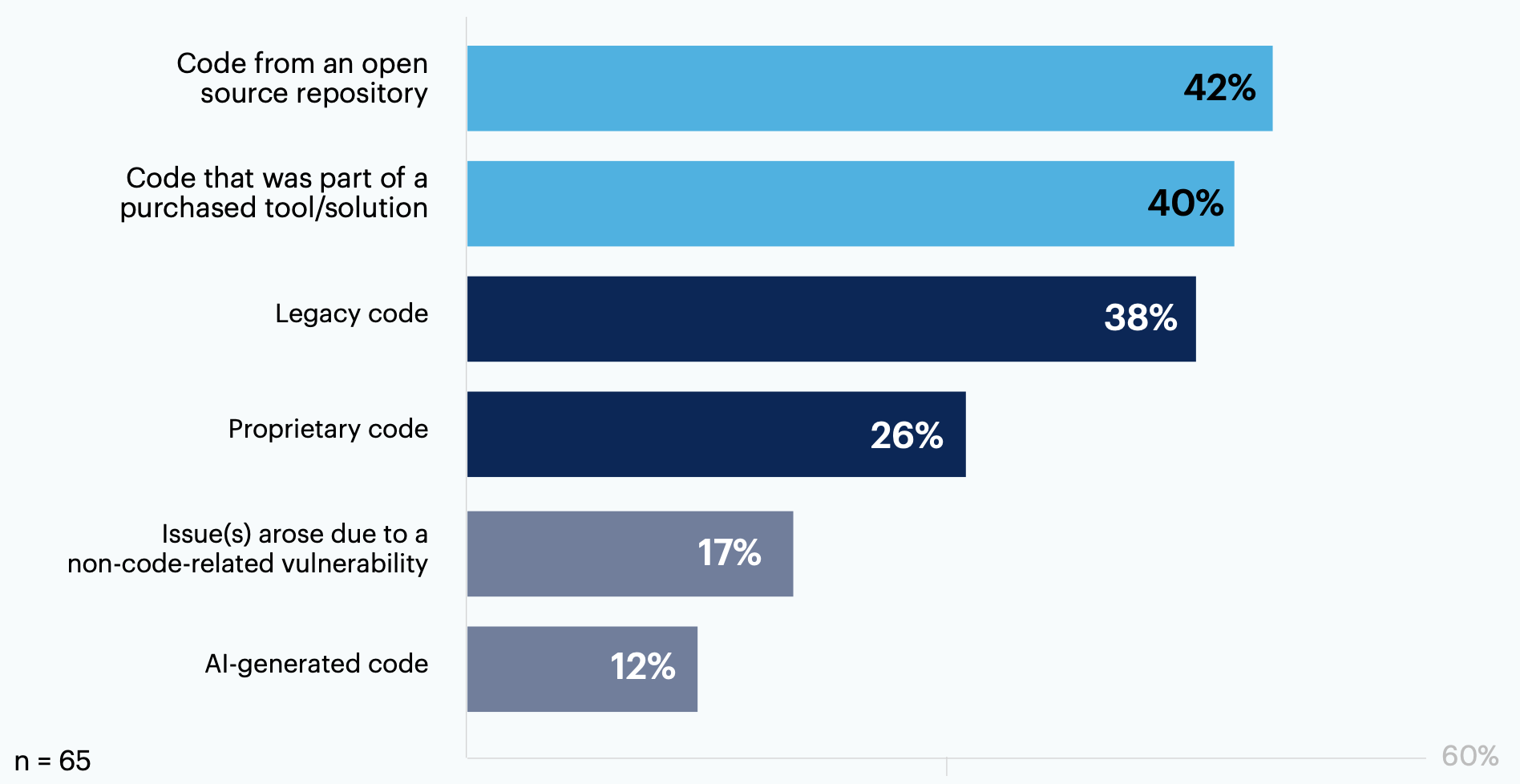
Among respondents whose organizations experienced a recent software-related security issue (n = 65), open source code (42%), code in purchased tools (40%) and legacy code (38%) were common sources.
Only 12% identified AI-generated code as the source of their recent security issue.
Thinking of the software-related security issue your organization experienced, where did the vulnerability occur (i.e., what was the entry point)? Select all that apply.
Acquired code from a recent merger/acquisition 11% | Can’t say 9% | Don’t know 2% | Other 0%
Question shown only to respondents who answered “Yes” to “During the past six months, did your organization experience a security issue(s) related to software?”
Nearly all (91%) of those respondent organizations (n = 65) have taken steps to improve their software security practices as a result of their recent experience. 8% plan to improve their security posture, but haven’t yet done so.
Did your organization take steps to improve software security practices after that issue(s)?
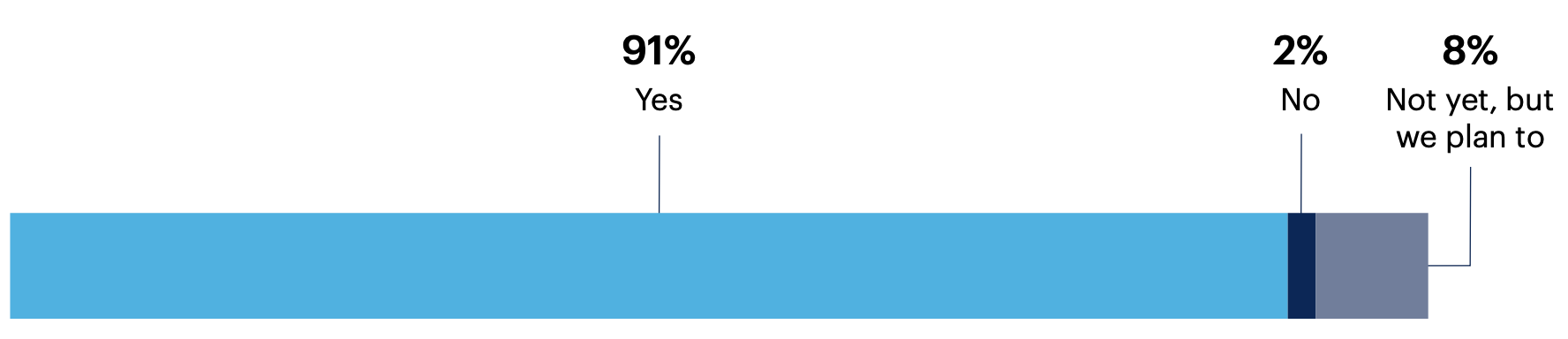
Don’t know 0% | Can’t say 0%
n = 65
Question shown only to respondents who answered “Yes” to “During the past six months, did your organization experience a security issue(s) related to software?”
Note: May not add up to 100% due to rounding
Question: In your view, what is the most important thing to remember about protecting against future software security risks?
Most issues happen due to internal hygiene. If we can emphasize more on that, we are mostly covered.
Always predict for variability in open source packages that have a massive adoption, like the JavaScript packages that have gone rogue recently.
For many, open source code is a potential risk source; organizations use VAs to gauge their risk exposure
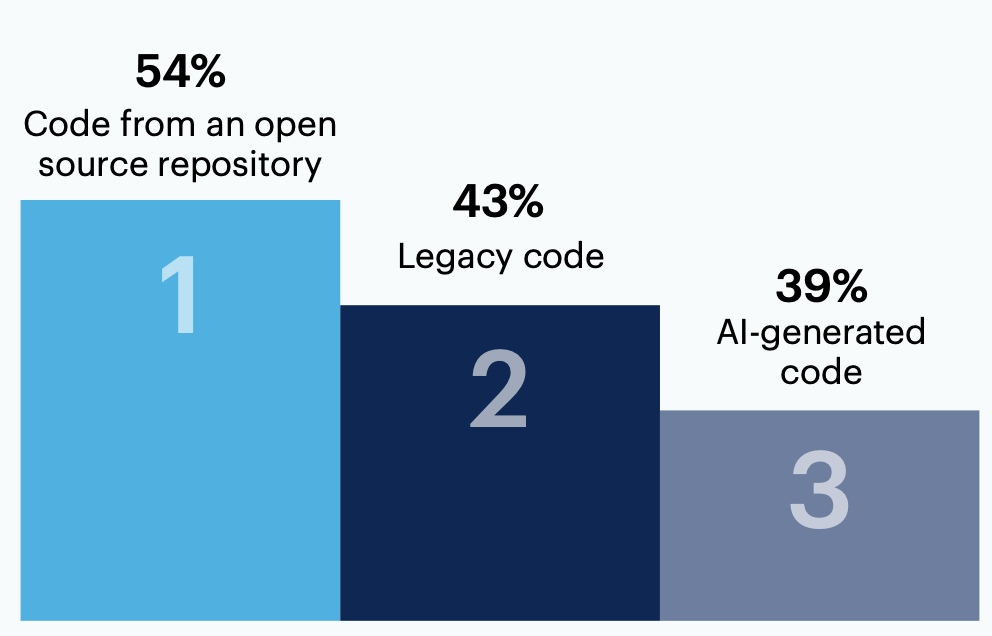
Many respondents (n = 125) anticipate that open source code (54%) or legacy code (43%) will present the most significant software security risks to their organization in the next six months.
Other anticipated risk sources include AI-generated code (39%) and code included in purchased tools/solutions (38%).
Thinking ahead: In the next six months, what code source(s) do you anticipate will present the most significant software security risks to your organization? Select up to three.
Code that is part of a purchased tool/solution 38% | Proprietary code 30% | Acquired code from a new merger/acquisition 20% | Can’t say 7% | Don’t know 2% | Other 0%
n = 125
70% of respondent organizations use VAs to gauge software security risk. Static code analysis (60%) and monitoring and observability (54%) are also common practices.
What process(es) does your organization currently use to assess software security risk? Select all that apply.
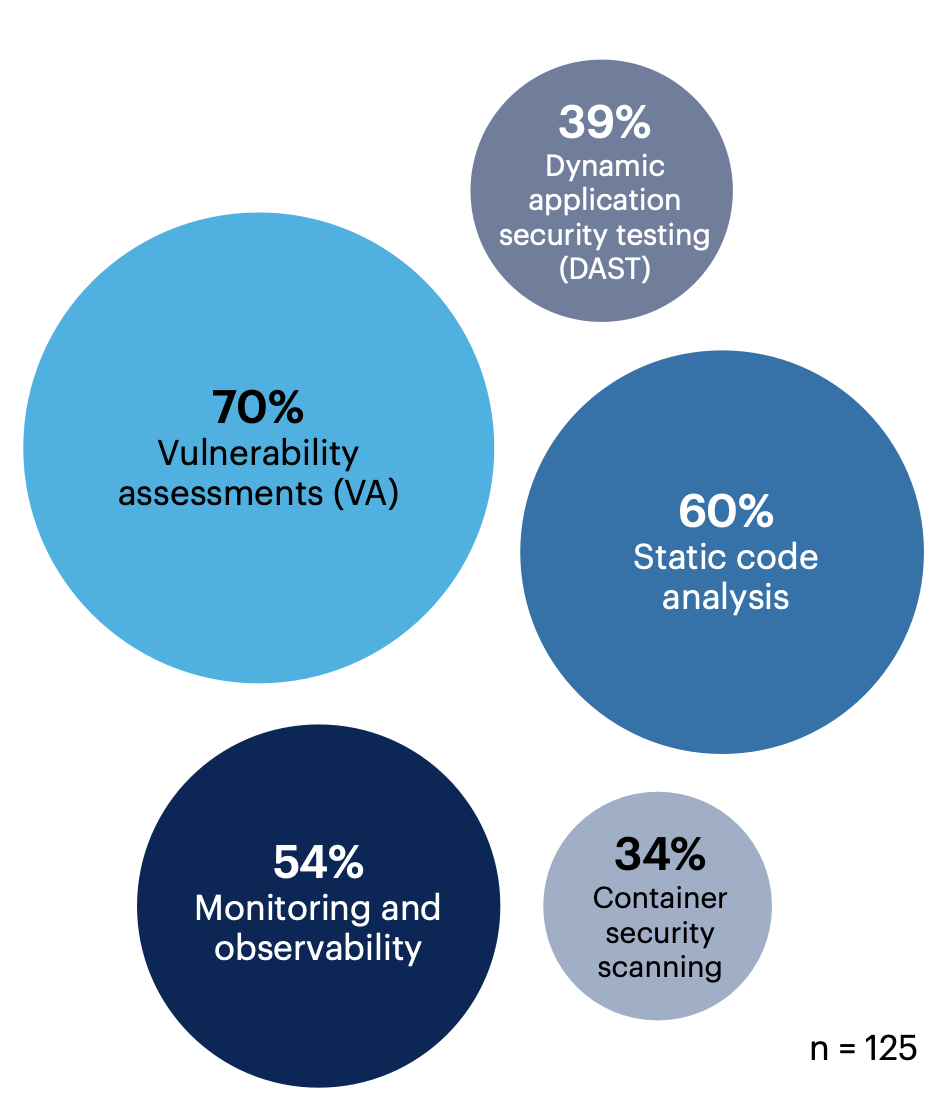
Static application security testing (SAST) 31% | Software supply chain management (e.g., requiring software bills of material) 25% | Software composition analysis (SCA) 22% | Mobile application security testing (MAST) 18% | Interactive application security testing (IAST) 17% | Risk scoring system 14% | Can’t say 6% | Don’t know 1% | Other 0%
In the next six months, 66% of respondent organizations plan to increase the level of investment allocated to assessing software security risk. 23% plan to keep their investment level the same.
In the next six months, does your organization plan to increase or decrease the level of investment (i.e., time, staff, tools) allocated to software security risk assessment?
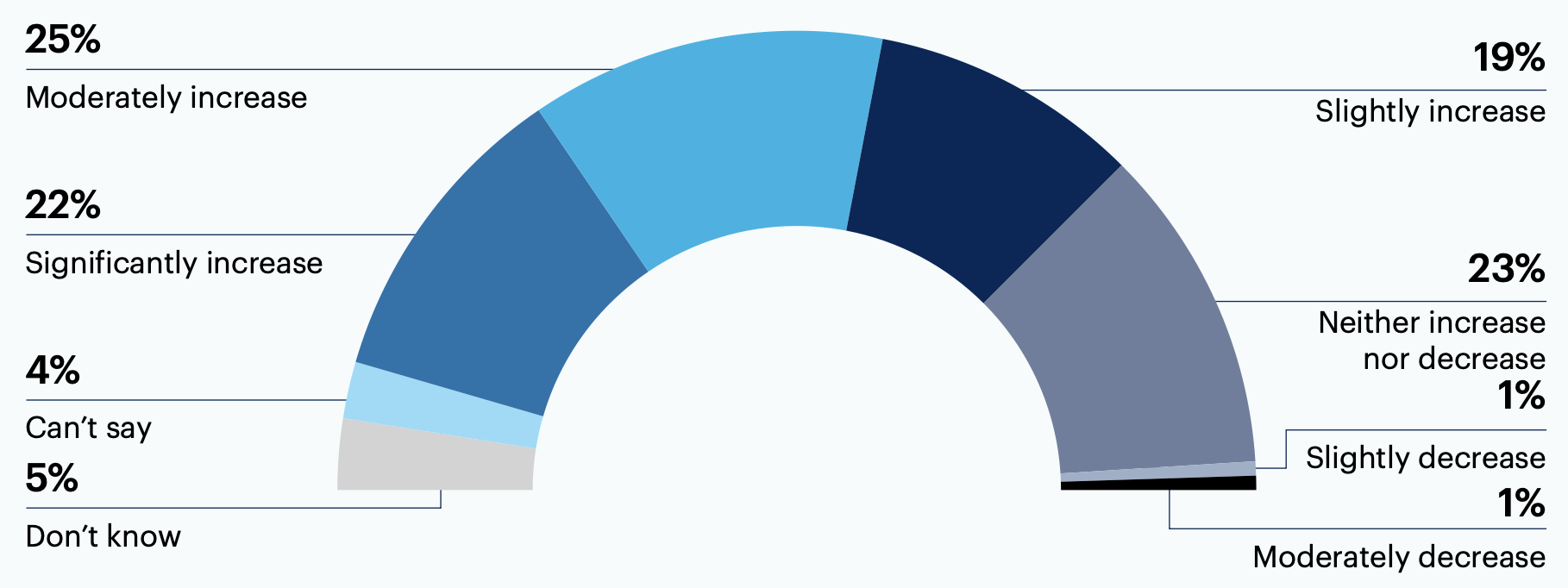
Significantly decrease 0%
n = 125
Question: In your view, what is the most important thing to remember about protecting against future software security risks?
Never assume you are done with security. It is a continuous activity.
Don’t trust code; verify it to the best of your abilities. Tools exist to help this, but you [must] always be thinking about security, not just of software, but of deployment chains and deployment stacks.
Tech leaders feel informed about emerging software security risks and are confident they can protect against them
How informed do you feel about emerging software security risks?
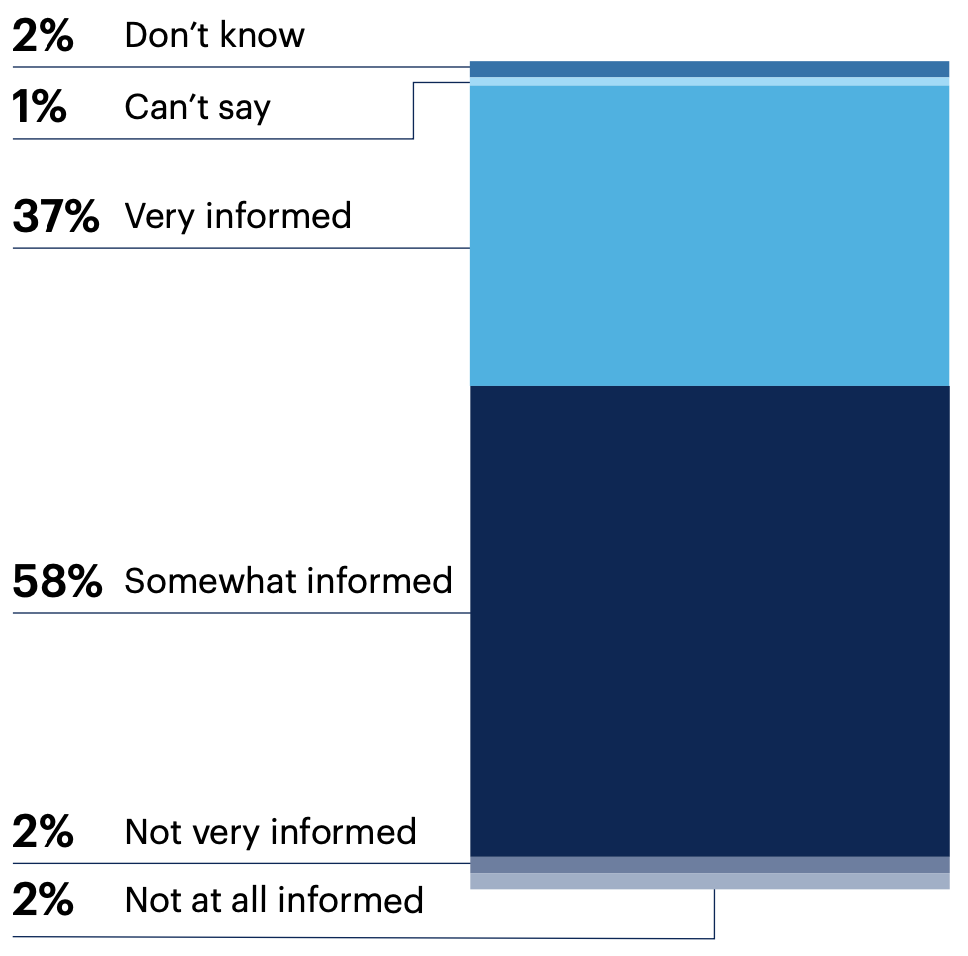
95% of respondents feel informed about emerging risks to software security.
n = 125
Note: May not add up to 100% due to rounding
Does your organization have security policies in place regulating the use of emergent technology and/or tools (e.g., generative AI coding tools)?
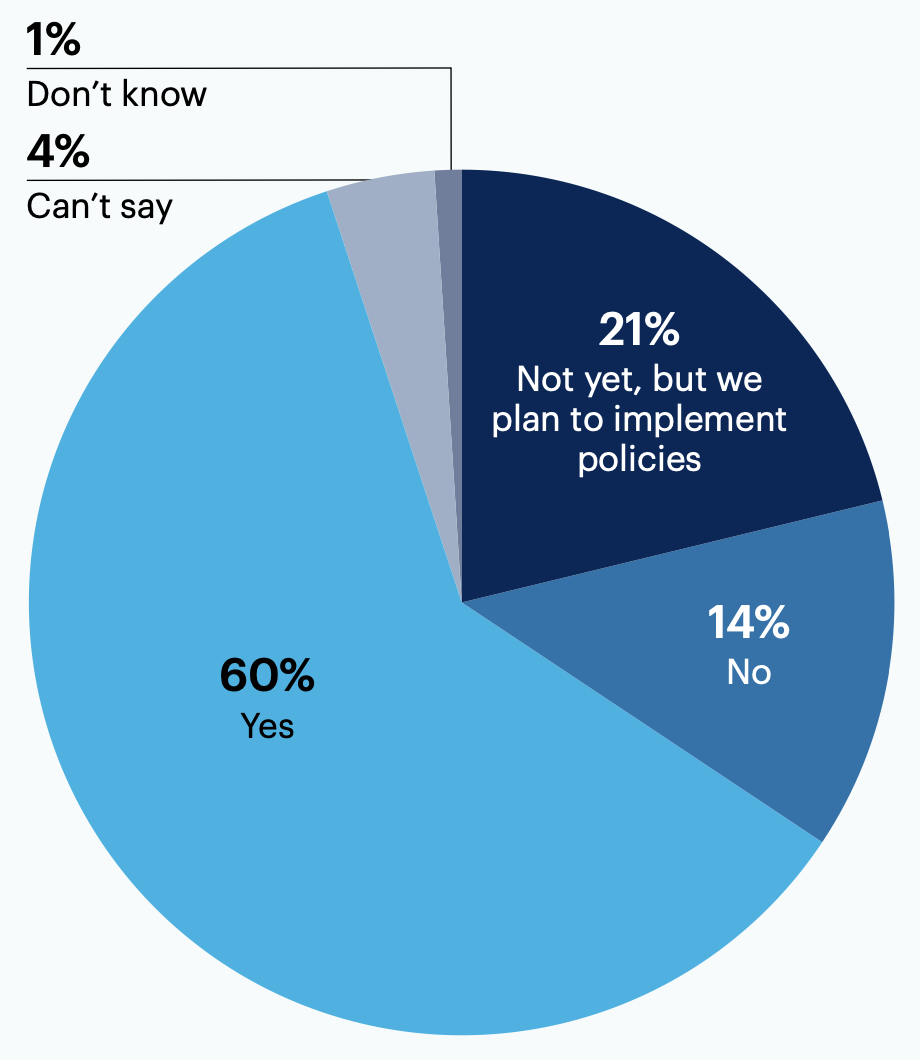
60% of respondent organizations have security policies in place that regulate the use of emergent tech such as generative AI coding tools. 21% don’t have policies yet, but plan to implement them.
n = 125
92% of respondents feel confident in their organization's ability to protect against software security risks in the next six months.
How confident are you in your organization’s ability to protect against software security risks in the next six months?
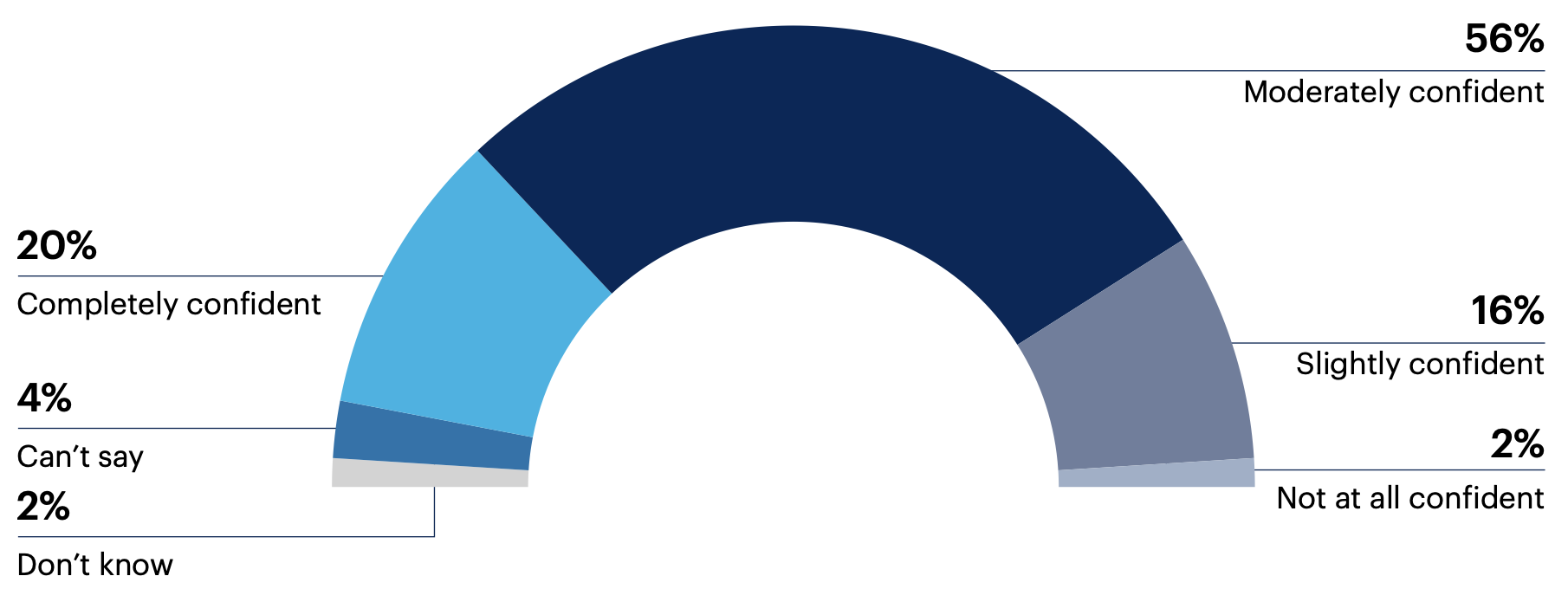
Too early to tell 0%
n = 125
Question: In your view, what is the most important thing to remember about protecting against future software security risks?
The future landscape of software security risk is still unpredictable due to [the] acceleration of AI tools on both sides of the equation.
Software security vulnerabilities are increasing due to exposure to third party libraries used.

Want more insights like this from leaders like yourself?
Click here to explore the revamped, retooled and reimagined Gartner Peer Community. You'll get access to synthesized insights and engaging discussions from a community of your peers.
Respondent Breakdown
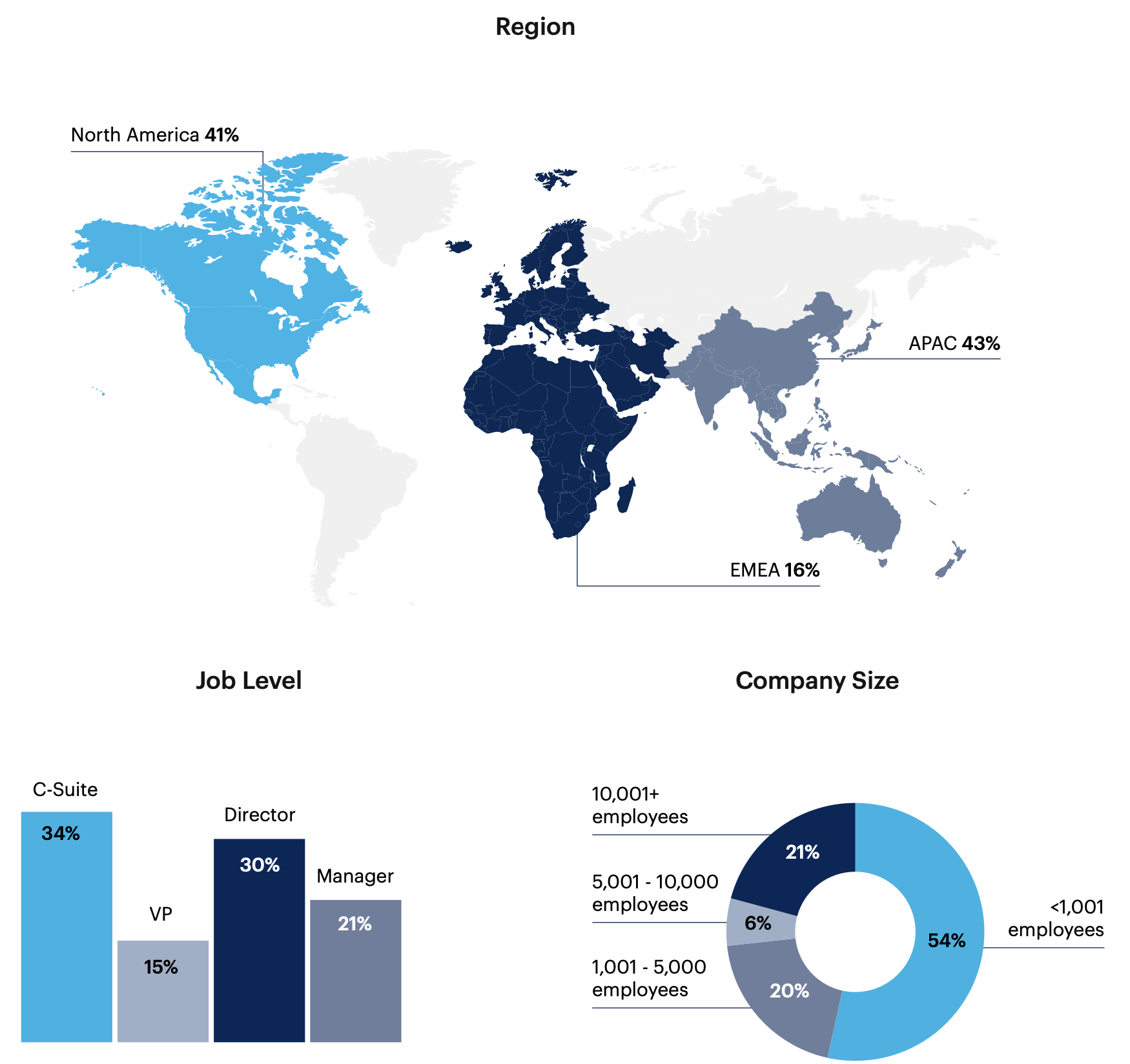
Note: May not add up to 100% due to rounding.
Respondents: 125 software engineering and information security leaders who are informed about sources of software security risk for their organization