Driving Cyber Maturity: Cybersecurity Program Management
Cybersecurity program management helps IT and security leaders evaluate and improve their organization’s security posture to achieve cyber maturity. How are leaders implementing cybersecurity program management and what impacts have they seen so far?
One minute insights:
 Most surveyed leaders have already implemented cybersecurity program management
Most surveyed leaders have already implemented cybersecurity program management Nearly all respondents report that cybersecurity program management has improved their security metrics
Nearly all respondents report that cybersecurity program management has improved their security metrics Commonly reported challenges include a lack of available staff, skills gaps and risk management program deficiencies
Commonly reported challenges include a lack of available staff, skills gaps and risk management program deficiencies Third-party services for cybersecurity monitoring and management are widely used among surveyed leaders
Third-party services for cybersecurity monitoring and management are widely used among surveyed leaders Most who have defined their program’s future state, or are working on doing so, say that there is cross-functional collaboration on this effort
Most who have defined their program’s future state, or are working on doing so, say that there is cross-functional collaboration on this effort
The majority have implemented cybersecurity program management and agree that it helps their communication with leadership/the board
Have you implemented cybersecurity program management activities and/or solutions?
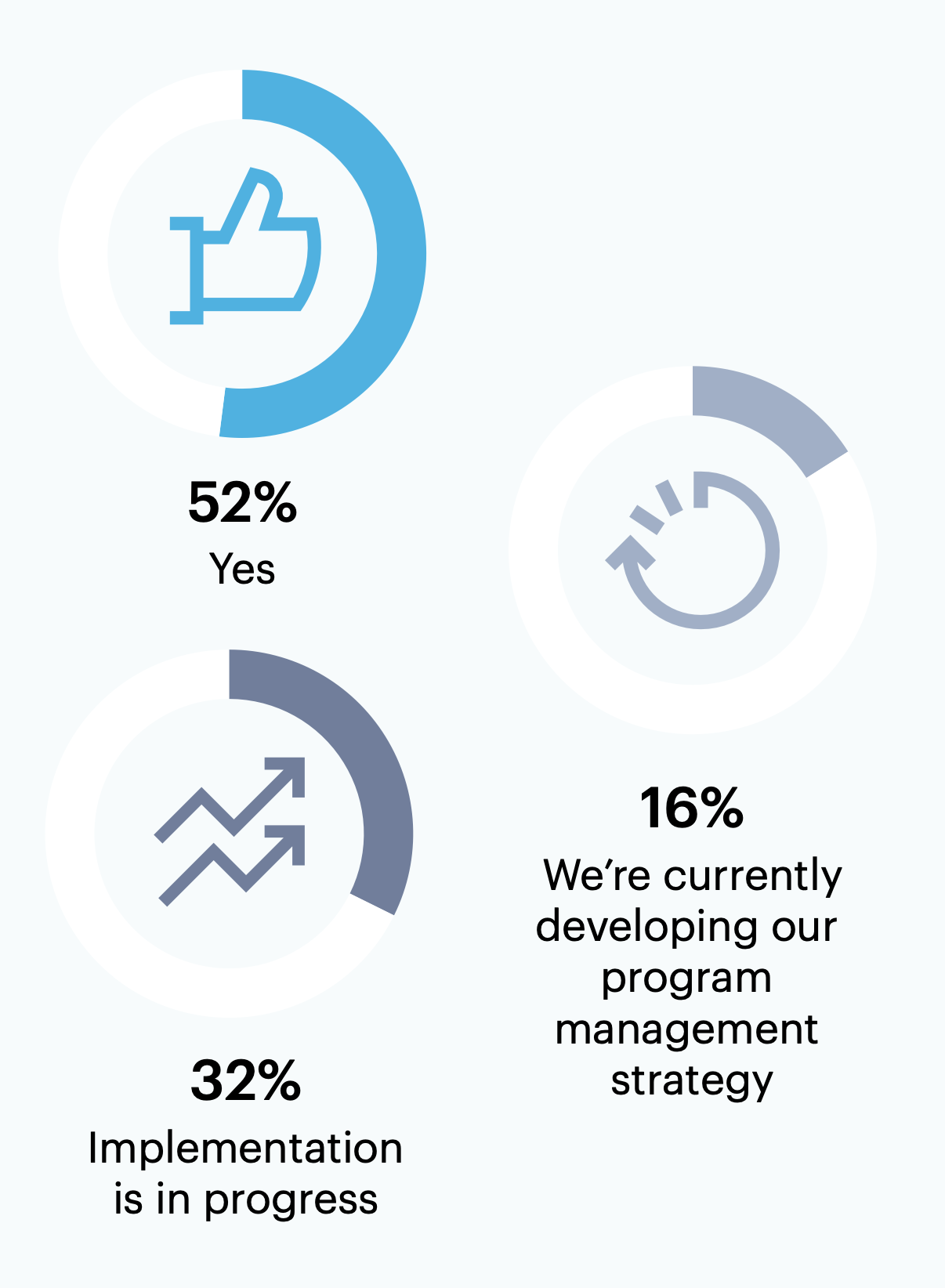
Over half (52%) of all surveyed leaders (n = 189) have implemented cybersecurity program management, and about one-third (32%) say implementation is in progress.
n=189
Respondents who answered “we intend to, but no plans are in place at this time” or “no” were eliminated from the survey.
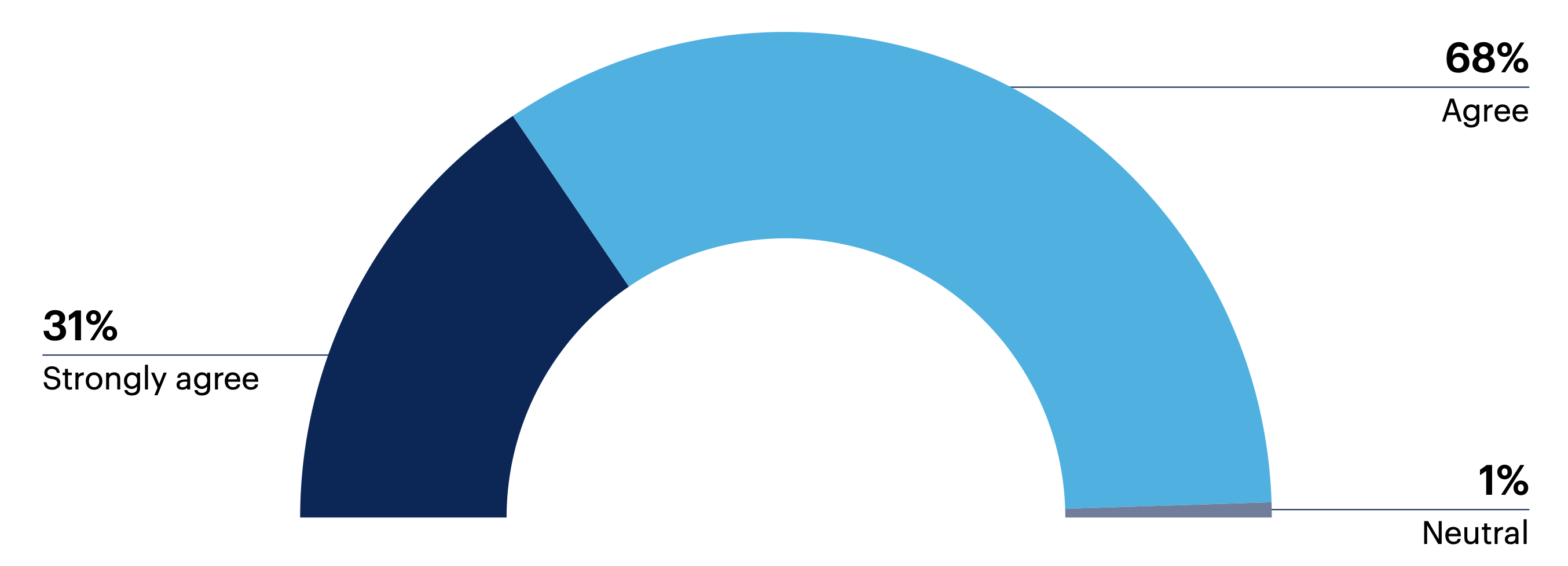
Nearly all (99%) of those who have implemented cybersecurity program management (n = 98) agree or strongly agree that it supports communication with leadership or the board as it helps them explain how business risk is impacted by program improvements and evolving threats.
Do you agree with the following statement: “Cybersecurity program management helps me explain to leadership/the board how program improvements and evolving threats impact business risk.”
n = 98
Disagree 0% | Strongly disagree 0%
Respondents who answered “yes” to “Have you implemented cybersecurity program management activities and/or solutions?”
Question: Do you have any final thoughts to share on cybersecurity program management?
This is for companies that have a high level of cybersecurity maturity. Like anything else, other areas within cybersecurity will be more important before you come to a point where you do [cybersecurity program management].
Industry-specific metrics and governance controls severely constrain maturity progress.
Threats are for real and much bigger than we initially thought. We can never be comfortable with what we have.
Cybersecurity program management improves security metrics but many face challenges with team availability and skills gaps
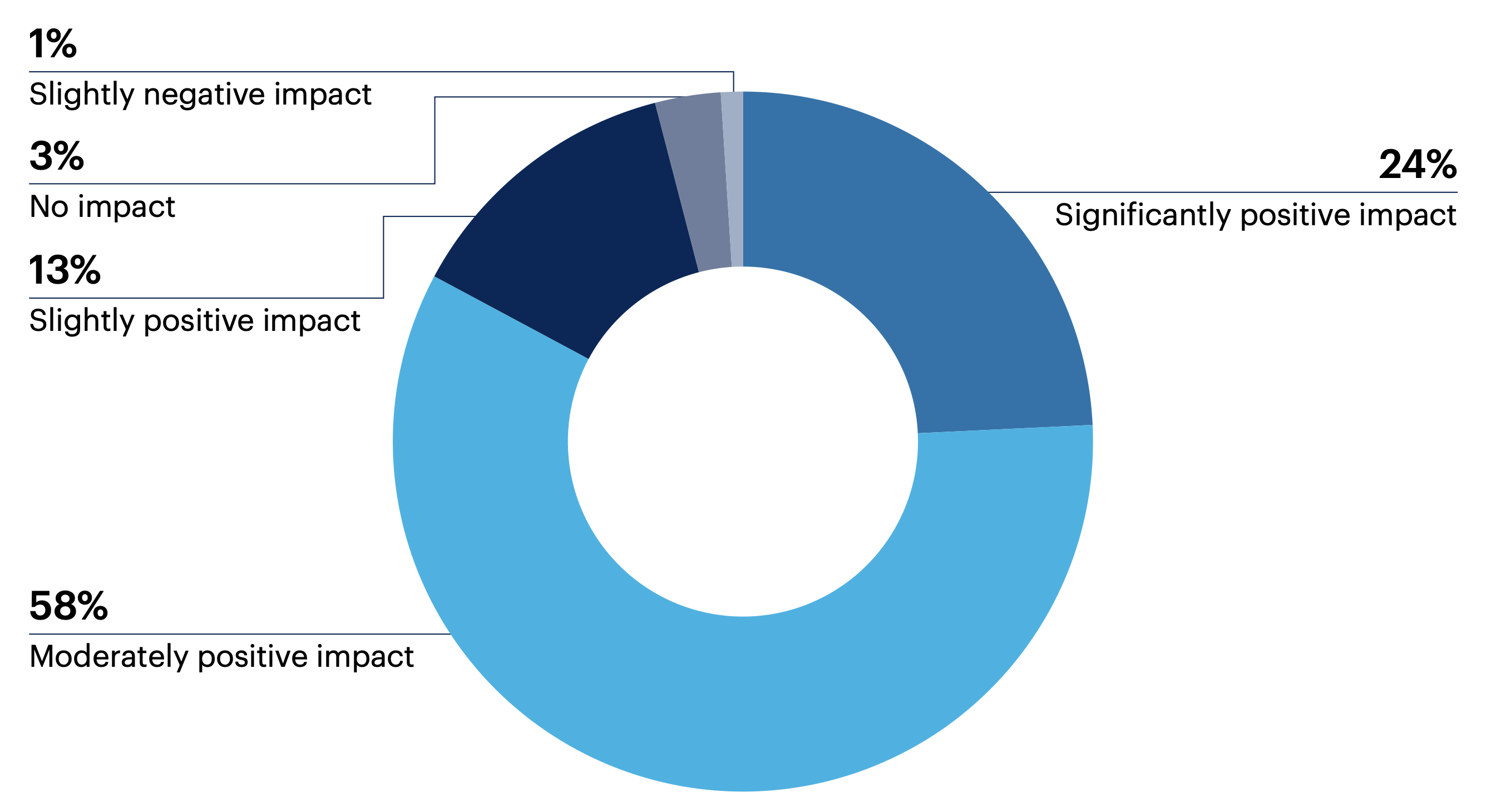
95% of surveyed leaders who have implemented (n = 98) cybersecurity program management say it had a positive impact on their security metrics, with about one-quarter (24%) reporting a significantly positive impact.
Has cybersecurity program management had a positive or negative impact on your security metrics (e.g., mean time to detection, mean time to recovery)?
n = 98
Moderately negative impact 0% | Significantly negative impact 0% | Not sure 0%
Respondents who answered “yes” to “Have you implemented cybersecurity program management activities and/or solutions?”
Note: Sum may not add up to 100% due to rounding
Among the same group (n = 98), the most commonly reported challenges faced in managing their cybersecurity program are a lack of available staff (46%) and skills gaps (45%).
About one-third are struggling with deficiencies in their risk management program (35%), inflexible governance processes (31%) and under utilized security tools or licenses (31%).
What challenges have you encountered in managing your cybersecurity program? Select all that apply.

n = 98
Insufficient reporting capabilities or metrics 29% | Controls provide inadequate visibility 24% | Documentation issues (e.g., not easy to access or understand for non-technical individuals) 20% | Out-of-date security tools 17% | Program doesn’t address technical skill sets outside IT 14% | Lack of collaboration between organizational stakeholders and security/IT staff 12% | Lack of consensus on risk prioritization 10% | Metrics lack context (i.e., metrics are not meaningful to leadership/board) 9% | Decision-making power lies outside of IT/security 6% | None of these 3% | Other 0%
Respondents who answered “yes” to “Have you implemented cybersecurity program management activities and/or solutions?”
Question: Do you have any final thoughts to share on cybersecurity program management?
We have evaluated a few vendors, and we feel a solid cybersecurity program for email phishing is missing from the vendors we evaluated.
Quite complex to wrap security around the IT systems and implement governance.
Distributed visibility seems to be a major issue for us — delegating segmented access to groups/divisions. Reporting can do it, but isn’t interactive.
Many use third-party services for cybersecurity program management and over three-quarters conduct regular threat assessments
What methods do you use or plan to use for cybersecurity program management? Select all that apply.
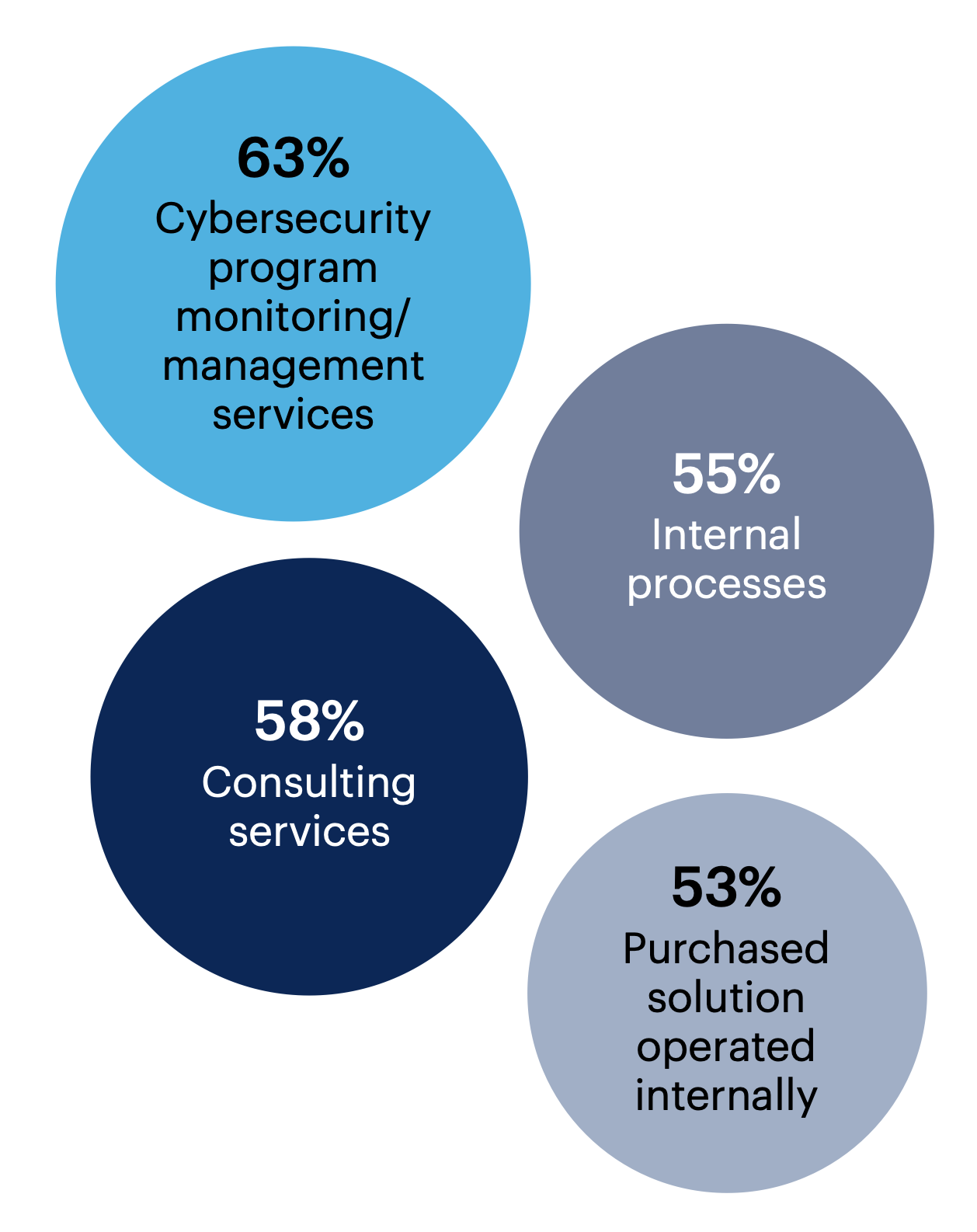
Most surveyed leaders who have implemented cybersecurity program management or are in the process of doing so (n = 158) look to third-party services for monitoring or management (63%) and 58% use consulting services.
None of these 1% | Other 0%
n = 158
Respondents who answered “yes” or “implementation is in progress” to “Have you implemented cybersecurity program management activities and/or solutions?”
From the same group (n = 158), most respondents either currently or plan to conduct threat assessments (80%) or risk evaluations (72%) on a regular basis, and over half cited regular reviews for policy (58%), incidents (56%) or controls (55%).
Just over one-third say they regularly conduct or plan to conduct assessments for applications (38%), training program validation (35%) or issue remediation (34%).
Which of the following assessments are or will be conducted on a regular basis (whether they will be done internally or using external consultants)? Select all that apply.
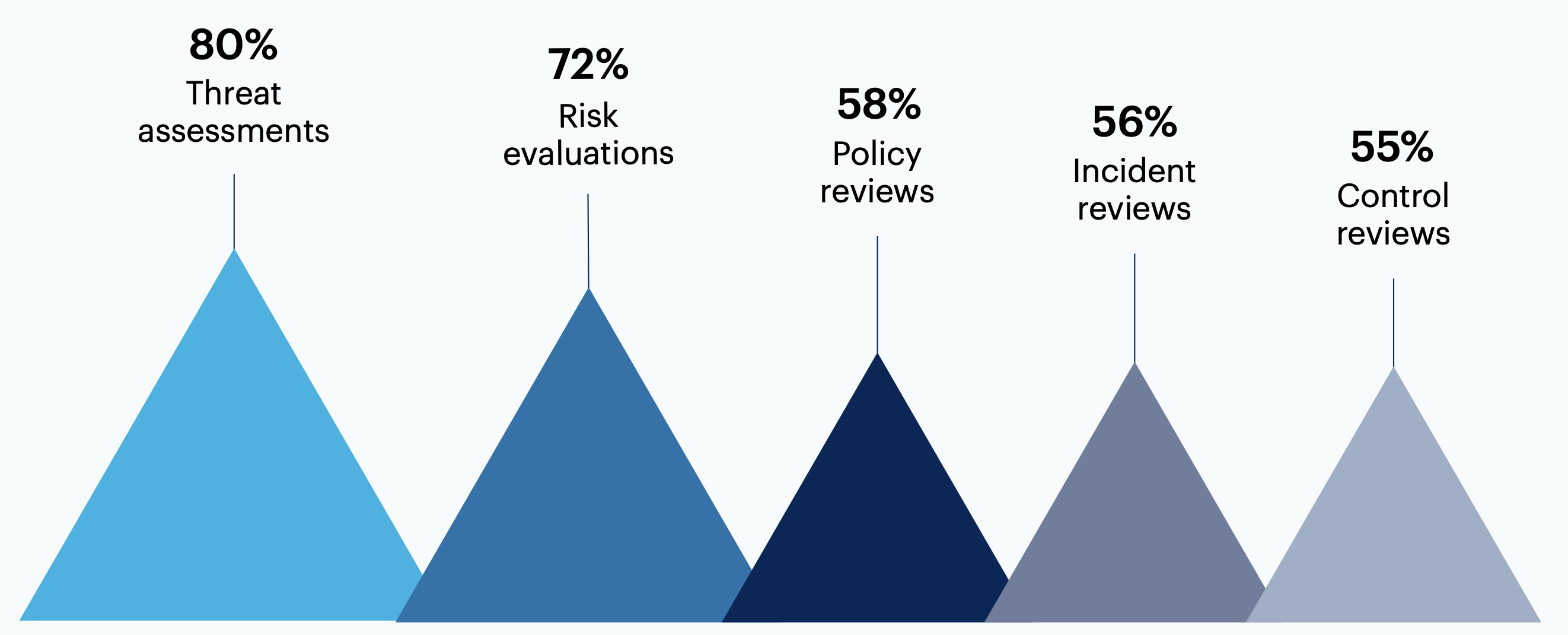
n = 158
System assessments 44% | Change management process assessments 43% | Application assessments 38% | Training program validation 35% | Issue remediation 34% | Baseline assessments 23% | Facility assessments 11% | None of these 0% | Not sure 0% | Other 0%
Respondents who answered “yes” or “implementation is in progress” to “Have you implemented cybersecurity program management activities and/or solutions?”
Question: Do you have any final thoughts to share on cybersecurity program management?
Although we have external companies who test our cybersecurity program, we intend to strengthen this as a form of training for our staff by doing more social engineering.
Cyber risk is a difficult area because the greater visibility we provide over vulnerabilities or gaps in our solutions, the more noise occurs. Unfortunately, executive teams have gotten into the habit of cyber risk as a zero-sum game, and unless you can show you have mitigated every risk, they will raise concerns. Trying to get executive teams to document their risk tolerance has proven unsuccessful.
Some have both a defined target state for their cybersecurity program and a roadmap to reach it; cross-functional collaboration in this area is common
Have you defined a target (i.e., future) state for your cybersecurity program?
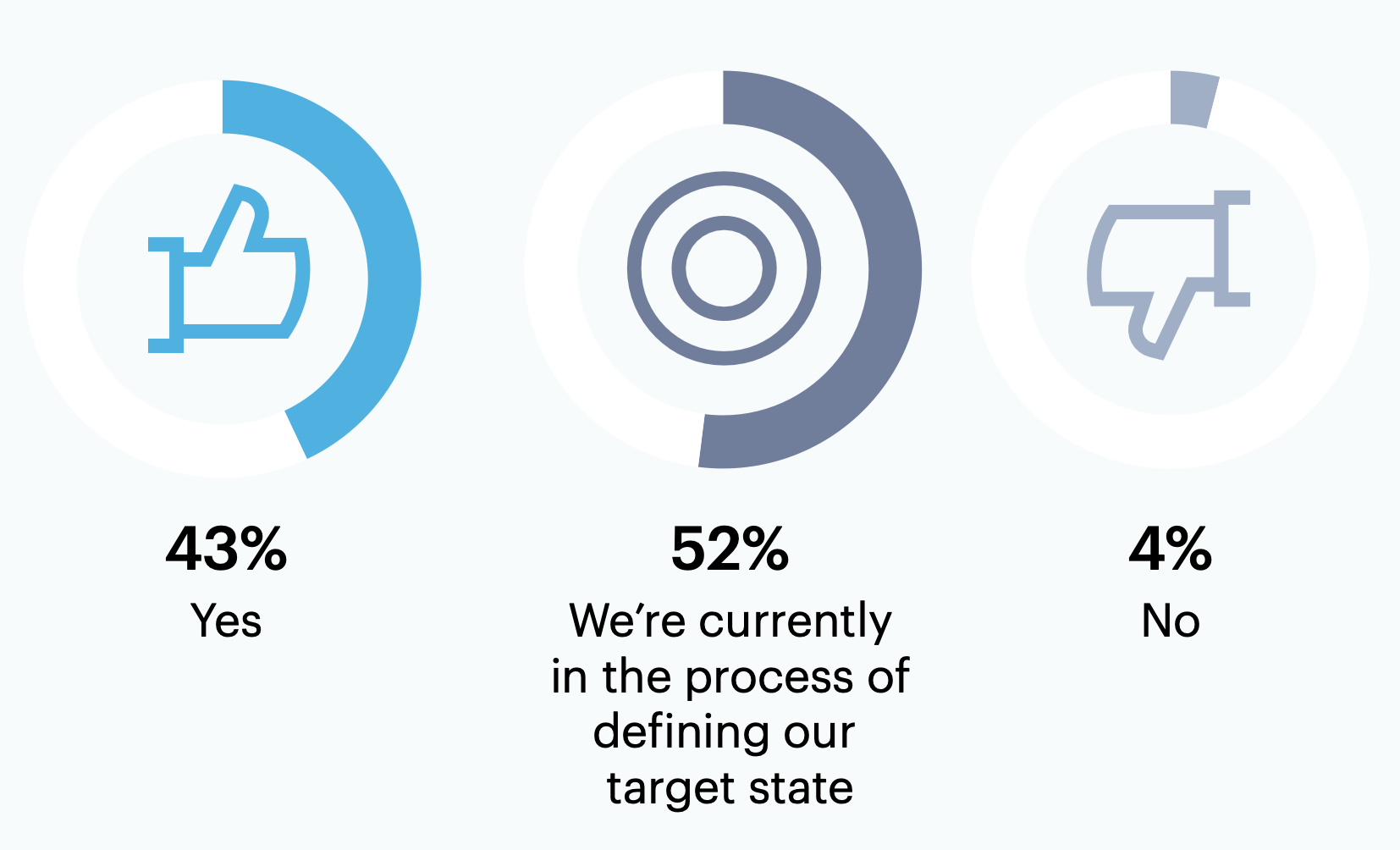
Out of all surveyed respondents (n = 189), less than half (43%) have defined a future state for their cybersecurity program.
n = 189
All respondents
Note: Sum may not add up to 100% due to rounding
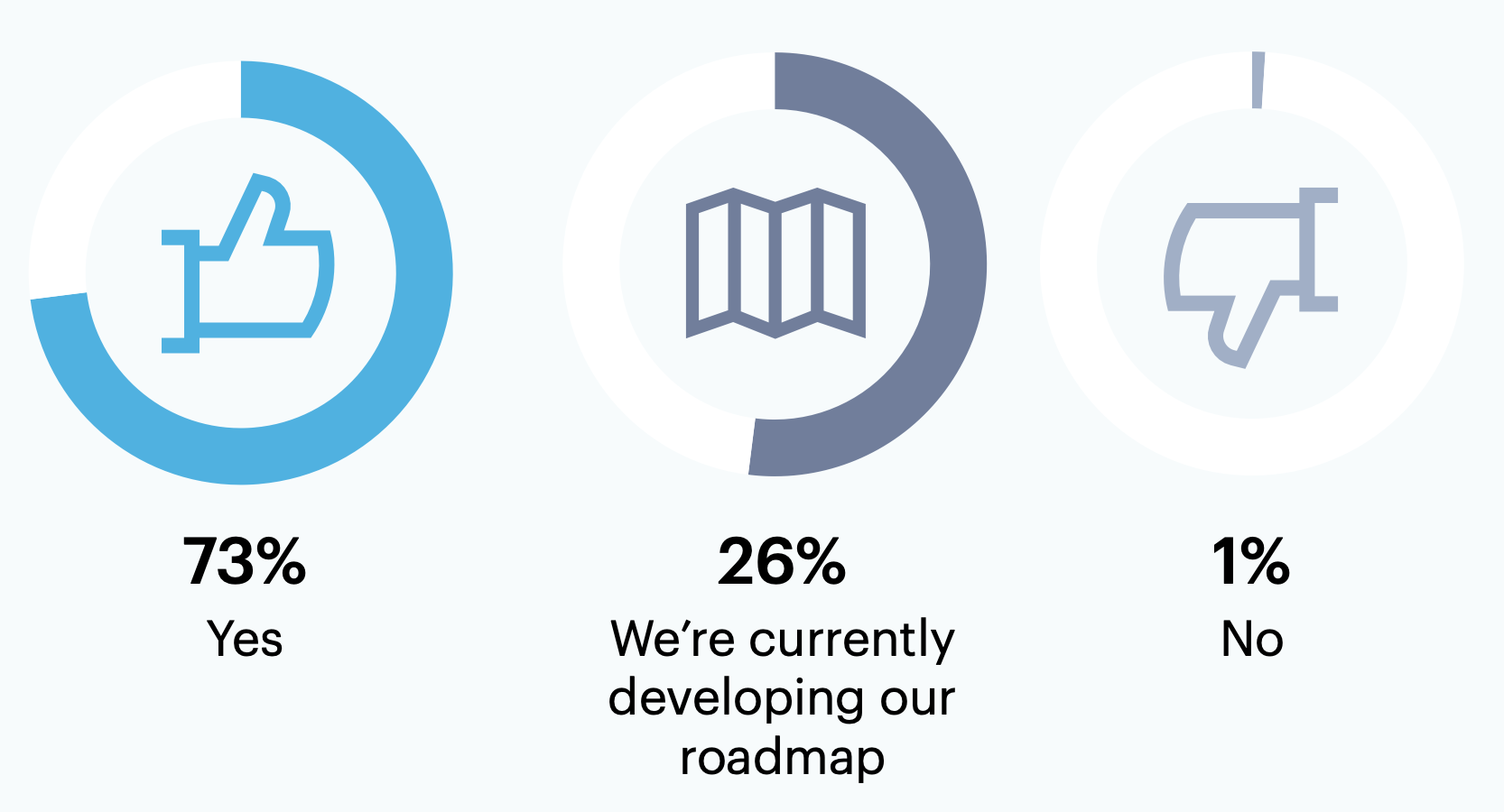
73% of those with a defined future state for their program (n = 82) have already developed a roadmap to achieve it.
Have you developed a roadmap to address gaps between the current and target state of your cybersecurity program?
n = 82
Respondents who answered “yes” to “Have you defined a target (i.e., future) state for your cybersecurity program?”
70% of surveyed leaders who have or are in the process of defining the future state of their cybersecurity program (n = 181) report that staff outside of IT/security also participate in this activity.
Are staff from other business units (i.e., individuals outside of IT/security) involved in defining the target state of your cybersecurity program?
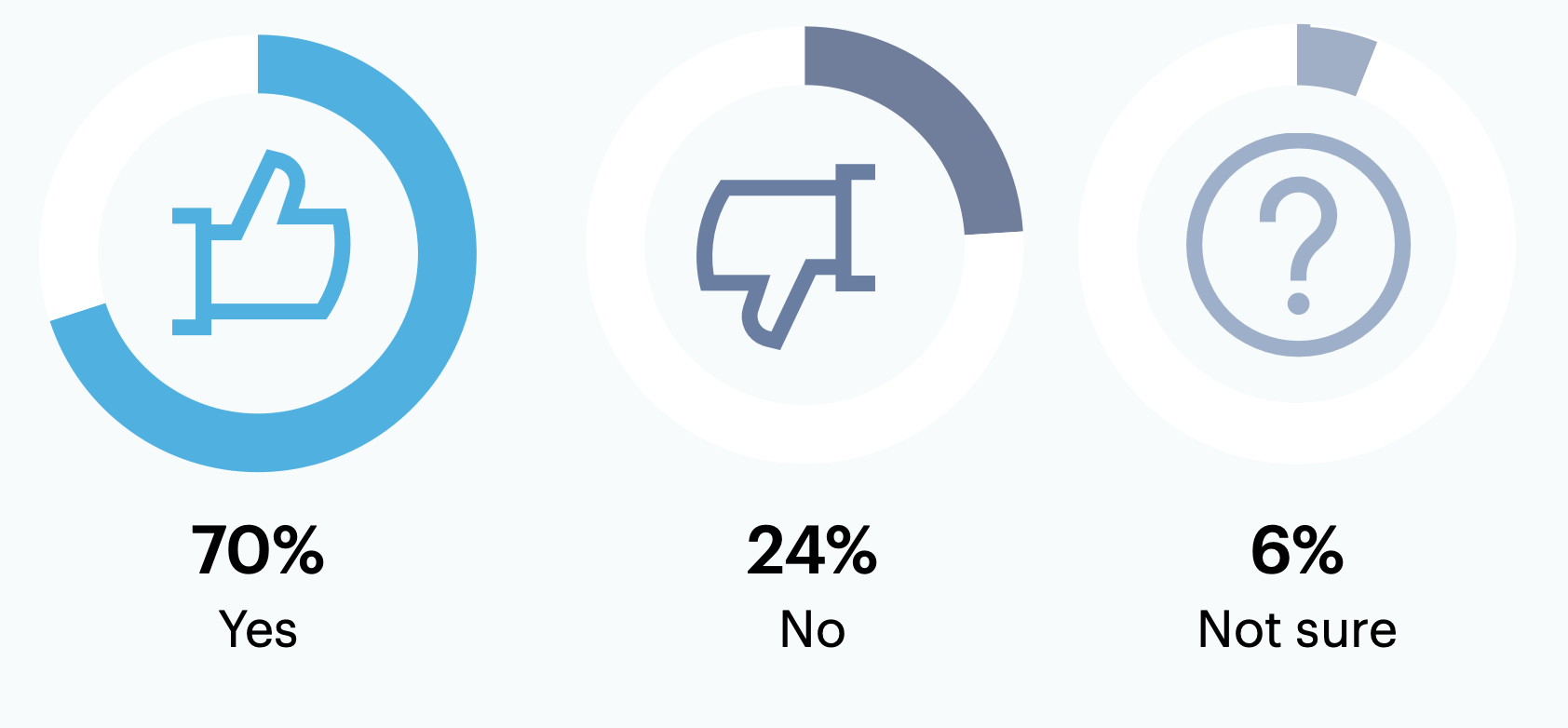
n = 181
Respondents who answered “yes” or “we’re currently in the process of defining our target state” to “Have you defined a target (i.e., future) state for your cybersecurity program?”
Question: Do you have any final thoughts to share on cybersecurity program management?
Maintaining end-user awareness/engagement continues to be a challenge even with awareness reminders/content, phishing campaigns and awareness training. So while most tools/platforms may help reduce the potential attack surface, having security-conscious employees is a continual goal to improve and educate.
There is a lot of work to still do, but we are making progress.
Our cybersecurity program management is a shared responsibility between IT (1st line of defense) and the business's internal risk management group (2nd line of defense).

Want more insights like this from leaders like yourself?
Click here to explore the revamped, retooled and reimagined Gartner Peer Community. You'll get access to synthesized insights and engaging discussions from a community of your peers.
Respondent Breakdown
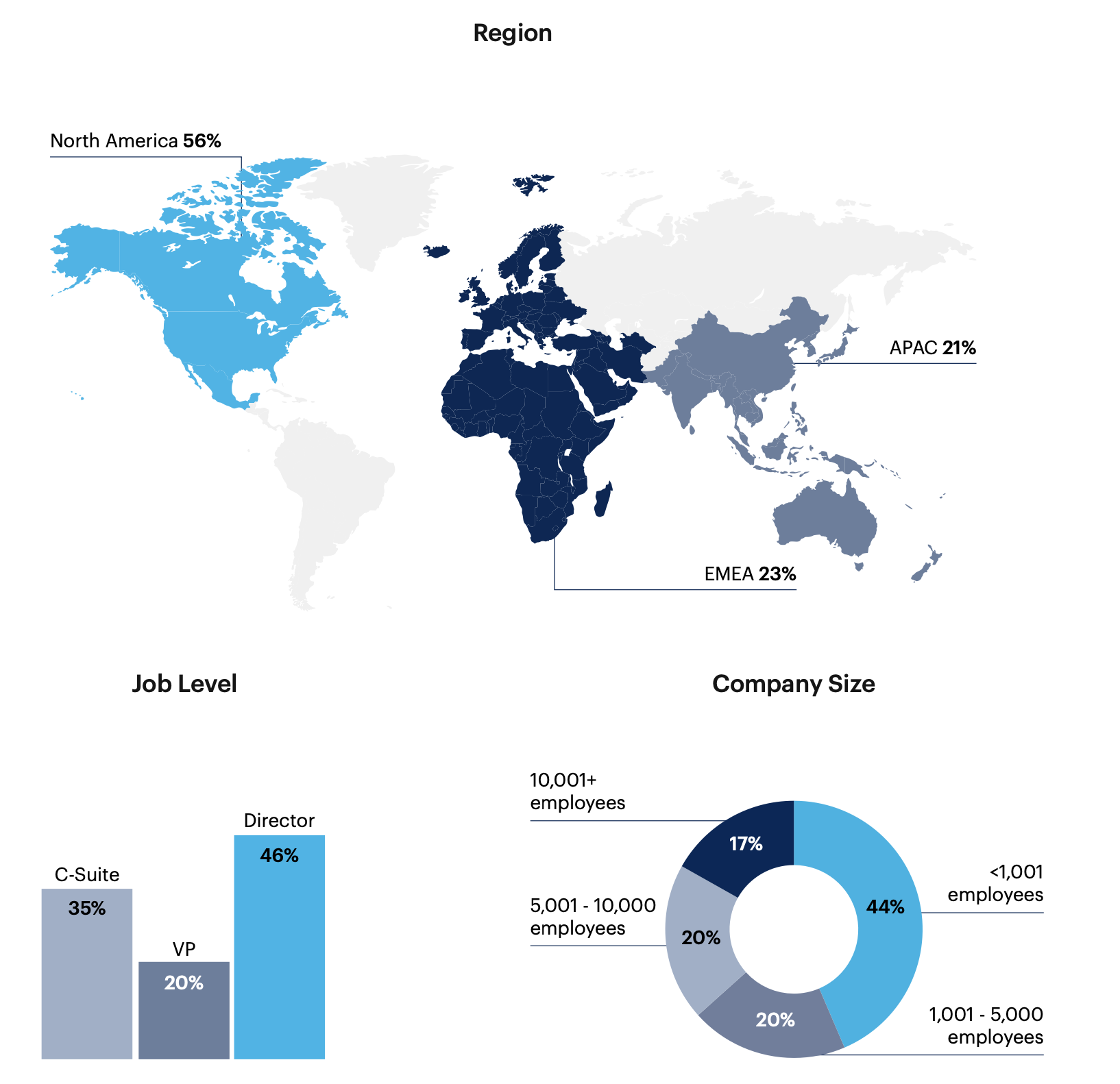
Note: Sum may not add up to 100% due to rounding